|
Fifth Dimension Catalog Contact Us |
|

|
What Are Cookies What are cookies
|
What Are Cookies
Back to the Table of Contents
A. What are cookies and are they dangerous to my computer or my privacy? No. A cookie is a simple piece of text. It is not a program, or a plug-in, and thus, it cannot access your hard drive. It cannot be used as a virus. Your browser (not a programmer) can save cookie values to its memory (RAM) or a file on your hard disk if it needs to, but that is the limit of its effects on your system. (See below for further explanation of cookies). A Cookie Alone Cannot Read Your Hard Drive To Find Out Who You Are, Where You Live, What Your Income Is, Or Other Personal Information. The only way that information could end up in a cookie is if YOU provide it to a site and that site saves to a cookie.
B. Can cookies fill my hard drive? NO. Most major browsers (Netscape & MS Internet Explorer) limit the number and size of cookies.
C. Am I at the mercy of the Web site when it comes to cookie control? NO. You have the power to set your browser preferences to reject cookies.
Why Do We Need Cookies
Back to the Table of Contents
Cookies are a very useful tool in maintaining state (persistence) on the Web. Unless something special is done, Web servers are only aware of users when a transaction -- sending or receiving information -- is in process. The moment the transaction is complete the server forgets about the user and makes no attempt to correlate subsequent transactions with previous exchanges.
An HTTP connection and transaction can be distilled into the following steps: 1. The browser contacts the server at the address specified in the URL, and requests a page, while providing its capabilities.
2. The server sends the state of the transaction back to the browser, together with the requested data or an error code.
3. The connection is closed and the server maintains no memory of the transaction.
Since the Web protocol, HTTP, is a "stateless" (non-persistent) protocol, it is impossible to differentiate between visits to a given web site, unless the server can somehow "mark" a visitor.
This is done by storing a piece of information in the visitor's browser, called a "cookie". Cookies can contain database information, custom page settings, or just about anything that would make a site customizable. A popular analogy is to the coupon you get from the dry cleaners. When you return for your clothes the dry cleaner matches up the tickets to ensure that the correct items are returned to you.
A cookie is simply an HTTP header that consists of a text-only string that gets entered into the memory of a browser. This string contains the domain, path, lifetime, and value of a variable that a website sets. If the lifetime of this variable is longer than the time the user spends at that site, then this string is saved to file for future reference. By default, cookies exist until the browser is exited; they disappear when you close the browser.
Users need to know that a Web site can only write and read the cookie for that given Web site. Only if the domain and path attributes match that of the host document (the default) can a cookie be stored or retrieved. There is still the perception that someone can read everything in the cookie file, which is 100 percent false. A Web site can only read what it put there. Nothing else.
The Bad Use of Cookies
Back to the Table of Contents
Privacy concerns:
How did I get a cookie from doubleclick.net? I've never been there! Is my personal information being hijacked?
DoubleClick.Net is an advertising company that is in proverbial hot seat because of its cookie tactics. A server cannot set a cookie for a domain that it isn't a member of. However, almost every Web user has gotten a cookie from "ad.doubleclick.net" at one time or another, without ever visiting there. DoubleClick and other advertisers have employed a clever solution that enables them to track users and serve media content without violating this rule.
To distill what a site like Doubleclick is doing:
Those little advertising graphics and "Top 5%" and "Browser Now" icons can serve more than one purpose. When you view a document containing such icons (say at FirstSite.com), your browser sends the matching cookie and the URL of the document on which the graphic appears to a second site serving the icon (eg. DoubleClick.Net). DoubleClick can eventually construct a database listing all documents (containing their icons) which have been viewed from the browser sending a specific cookie, via the first site. This database would accumulate a detailed profile of the user of that browser (you).
Further, if you provide any personal information at the first site, such as via a registration form, this information may be associated, using such a cookie and referrer field database, to your clickstream through all participating sites. In other words, these technologies make it possible for you to be easily followed through "cyberspace", regardless of whether you browse from home or office. Sites carrying this kind of advertising could be compromising (betraying?) your privacy.
This usage of cookies is the most controversial, and has led to the polarized opinions on cookies, privacy, and the Internet. Regulatory committees are currently working on proposals to ban or limit this kind of cookie usage.
The Good Use of Cookies
Back to the Table of Contents
Cookies have obvious appeal for corporate Webmasters because they deliver a fairly standard infrastructure to compensate for HTTP's stateless nature. That is essential for anything beyond the most rudimentary online order system, to make it possible for users to customize their interaction with large complex Web sites, and to customize the way they view a Web site.
For some situations, the cookie offers the best and most practical business solution. One example is an online shopping site. The site's Webmaster can use cookies to implement a shopping cart, thus allowing customers to spread a single shopping session across several visits to the site. Nominal customer information and shopping cart items can be stored in the cookie file, and recalled whenever the user revisits the online mall. In most cases Web sites store minimal information in the persistent cookie on the user's system but use the cookie as an index into its database where more details, like customer info and shopping cart items, are stored.
Netscape Communications and Amazon Books use a temporary cookie to maintain state information for shoppers. This enables a site to spread products and information over multiple pages, or to put the order entry forms on a separate page. As the user selects products they want to buy, the server indexes these selections to the session key carried as a cookie by the user's browser.
Persistent cookies -- those stored on the user's file system -- also provide a convenient location to store user preferences that are likely to be used each time the user visits a Web site. Netscape uses a simple cookie to enable a user to set a preference for viewing its site with or without frames. Search sites such as Excite and Search.Com also use cookies to customize what kind of information the user prefers to see when they log into the site.
Cookies can be used to store registration information so that a user does not have to enter a login and password each time they visit a site. Macworld Club, HotWired, and The New York Times stores the information necessary for entrance in a persistent cookie. If a user loses or discards the cookie they simply need to go through the manual login process which can also establish a new cookie.
Session vs Persistent
Back to the Table of Contents
Simply put, a SESSION cookie resides in the browsers memory and not on the hard drive. It can be used in conjunction with data stored in a login database to regulate participation in a Web site's service. When the user closes the browser or the user surfs to a new site the session cookie is either dropped or written by the browser to the hard drive for later reference. The cookie written to disk is called a PERSISTENT cookie, which can be referenced by the browser on behalf of the current Website.
One good use of persistant cookies is for preventing duplicate user ids from being used. Persistent cookies let Web sites tpo recognize someone who visited a site say a month ago, and they do not need to regenerate a new user id for the returning visitor.
Each time an established user logs into a restricted site, the Web server and database compares the browser cookie against the database record. Each connection attempt is logged, together with a variety of tidbits, such as browser type, IP address, and operating system. If the browser cookie and the cookie stored in the server database match, access is granted and the cookie is replaced with a new unique identifier. This prevents others from using your login name and password because their cookie (or absence of cookie) will not match what's in the server database.
If cookies are not used to store session ids assigned by the site then other methods for maintaining state include: 1. Passing the collected info between pages thru the URL, like http://thesite.com/login.html?ID=1234%Name=Bob+Smith%SSN=111-22-3333%Amount=$1000
2. Passing the data between pages in hidden HTML fields, which are actually passed in the HTTP header.
Both methods have limitations in length. And more importantly, they both expose their data during transmission (unless used in a secured session using something like Secure Sockets -- SSL). Whereas cookies containing only session ids pass cryptic info over the internet, and the receiving Web site uses that session id to look up the users data, thereby alleviating the need for secured sessions over exposed connections.
The Bottom Line
Back to the Table of Contents
The users have the power to reject cookies, so if the Web industry wants to use them they're going to use them responsibly. Privacy policies should be developed that give users proper notice, choices, and security, on what information is being saved in cookies and how they handled.
Your Choices With Cookies
Back to the Table of Contents
You can choose your cookie options when you set up your Preferences.
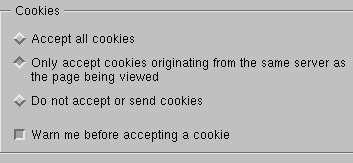
How can I protect my privacy?
from Alexandra
In the above example -- I only accept cookies from the same server. I also want to be warned. I periodically erase the information in the cookies file.
Statements like the following from websites that ask for my personal information, make me very nervous
This information may be shared with our business partners on an aggregate basis only. The purpose of sharing this information is to help our business partners understand our customers.
another
...We also provide Personal Information to our vendors and suppliers where it is necessary for them to provide us with products and services related to better operation and maintenance of our website ("Vendors"). We will attempt to require that each of these Vendors not further use or disclose your Personal Information for any purpose other than providing us or you with products and services. Of course, we cannot guarantee their compliance with these restrictions
Other References and Sources of Information
Back to the Table of Contents
http://www.cookiecentral.com
http://www.junkbusters.com
http://www.epic.org/privacy/internet/cookies
|
You are welcome to share this © article with friends, but do not forget to include the author name and web address. Permission needed to use articles on commercial and non commercial websites. Thank you. |